Getting Started with Trustnest IAM
Concepts
All trustnest cloud resources are linked to an azure tenant and an azure active directory. To make it as simple as possible, all trustnest resources are associated to a single tenant (Thales group tenant). However, there is different Azure Active Directories on Trustnest.
Of course, IAM manipulates objects representing users but also technical accounts. Be careful, there are multiples types of technical accounts depending on the type of resources you want to manipulate (azure or COTS).
HOWTO
How to select the right tenant ?
Trustnest IAM implements few security guidelines to limit the risks. To avoid asking the support unauthorized permissions, we have put in place different uses cases:
TrustNest Identity and access Management supports the following use cases:
Use Case A: Management of Thales employees and contractors developing directly on Trustnest (deployment of cloud resources as developer and devops)
Use Case B: Management of Thales employees and contractors accessing to Function SaaS Services (Software Factory, PostIT, O365 thalesdigital.io tenant)
Use Case C: Management of Thales employees, contractors and partners accesses to SaaS services (product developed on trustnest)
Use Case D: Management of any external accesses to SaaS services (product developed on trustnest)
You will find more details on each previous use cases by looking at the IAM service offer page - website
If you want to deep dive on this topic, you discover few architecture views on IAM & gitlab - auth required
What are the user identity naming convention ?
Users: A user is a human, authenticated to Trustnest IAM using several authentication mechanisms (minimum: credentials + microsoft authenticator mobile application; and for specific use cases: the compliance of your laptop )
Depending on your function and the link with Thales, you will have a specific email address. Discover the naming convention page - auth required
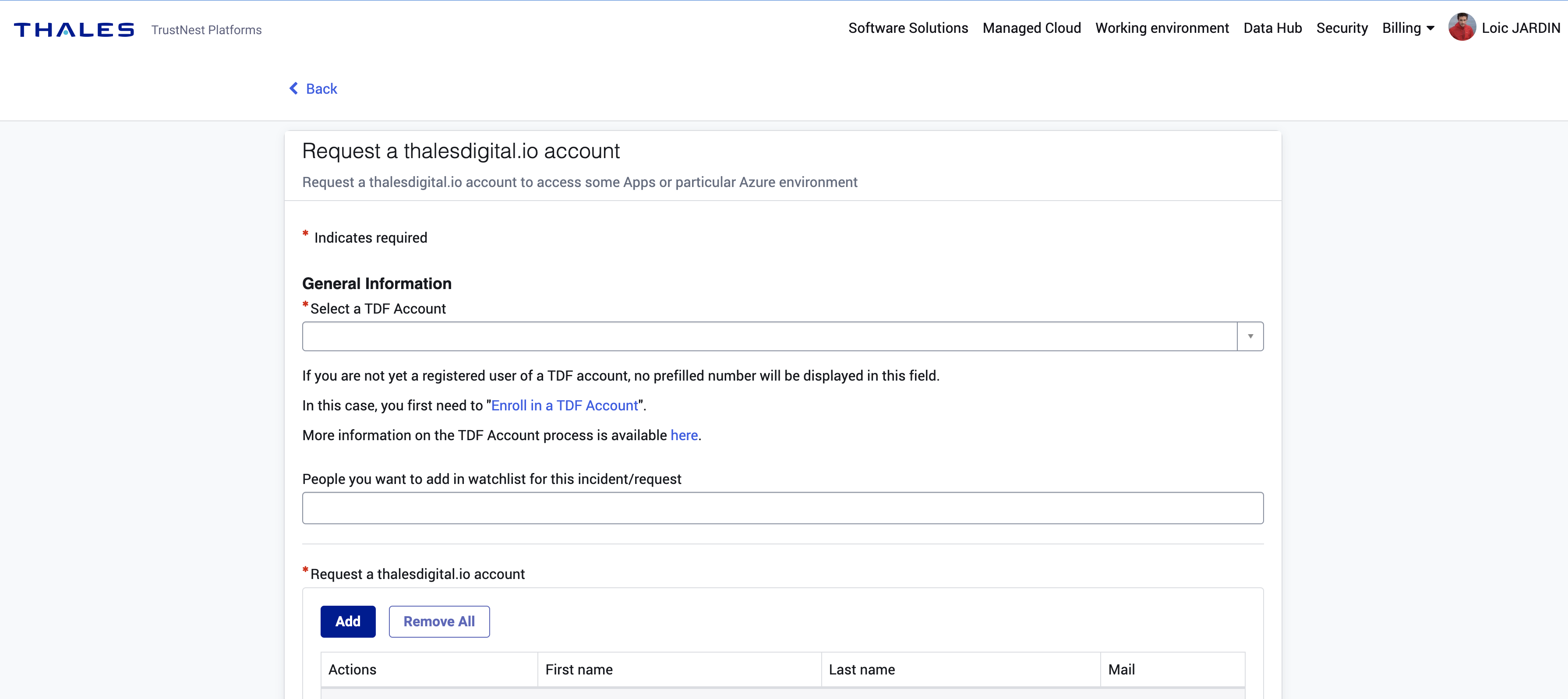
How to ask for a user creation ?
Simply go to postIT and select Request a thalesdigital.io account
What type of technical accounts are available ?
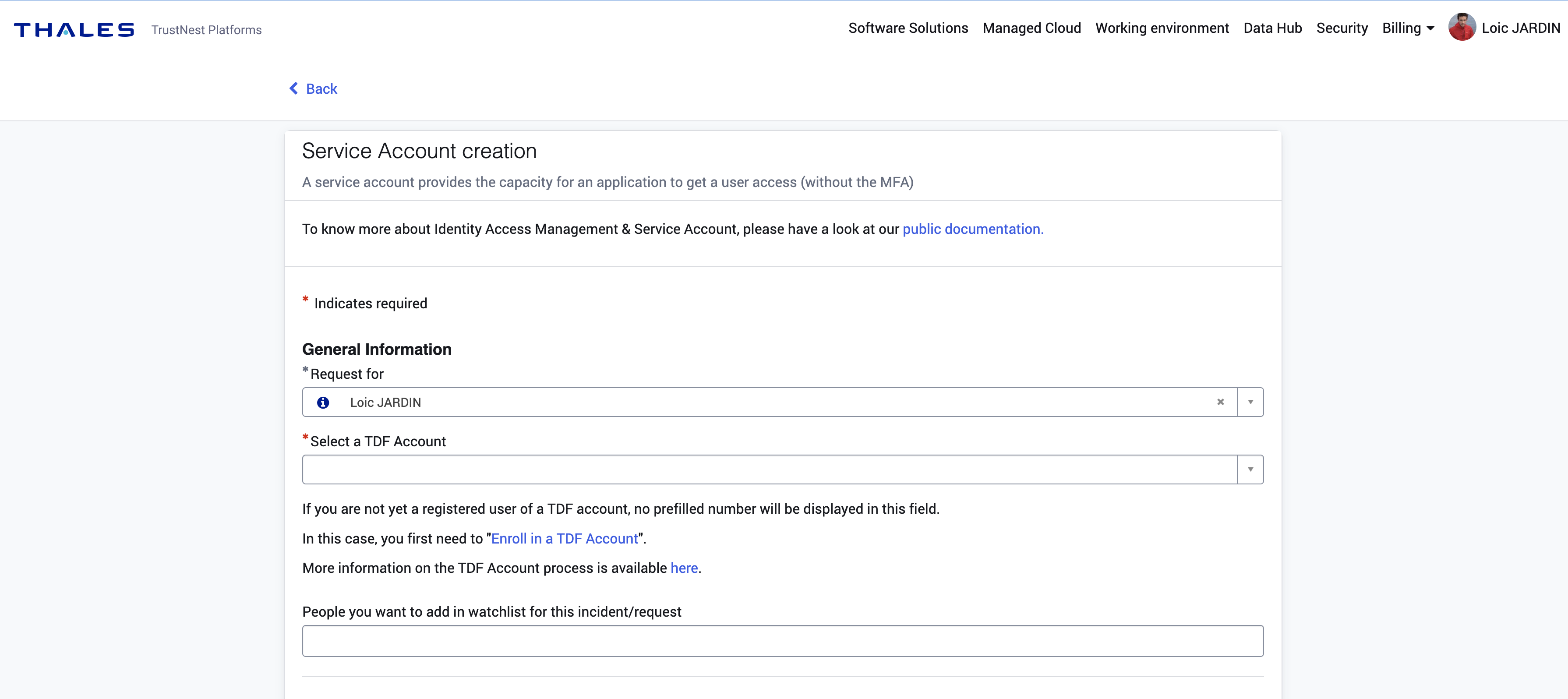
Service Account: A service account is a technical account to get an identity (without MFA) to Trustnest COTS. Usually, the name of the account contains "svc" prefix in the domain. Warning: most COTS provides token generation (associated to a user) --> make sure you need absolutely a service account BEFORE requesting it.
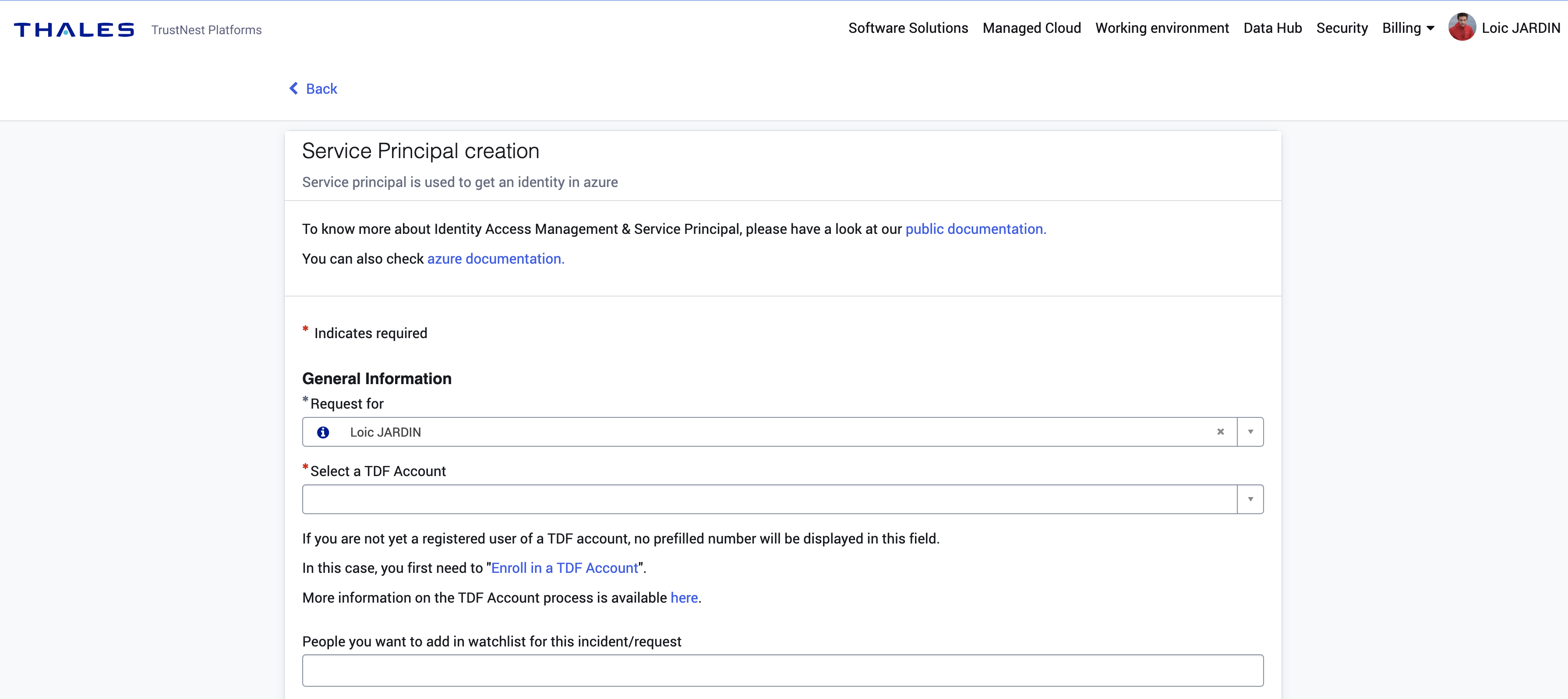
Service Principal: A service principal is also a technical account to get an identity (without MFA) to Azure. Warning: SP must follow minimum privileges because the lack of MFA is security vulnerability.
How to ask for Service Account ?
Simply go to postIT and select Service Account creation
How to ask for Service Principal ?
Simply go to postIT and select Service Principal creation
Next steps
- Grant access of service account to Software Factory: Get access to Software Solutions
- Grant access of service principal to an azure resources: Go to the azure resource, check RBAC and grant permission to your service principal (you should see it by searching the name)
- Grant access of service principal to azure active directory: Add Service Principal permission
Granting access of service account to azure resources does not make sense. You should look at service principal to do it. Also, granting access of service principal to COTS like gitlab or artifactory does not make sense too. You should look at the service account to do it.