Service Account Creation Form
Context
Service Account: A service account is a technical account to get an identity (without MFA) to Trustnest COTS. Usually, the name of the account contains "svc" prefix in the domain. Warning: most COTS provides token generation (associated to a user) --> make sure you need absolutely a service account BEFORE requesting it.
The direct permission to create a service account is not provided to our users because Azure Active Directory does not provide sufficient fine grain rbac. Instead, Trustnest provides a form to request it. The purpose of this documentation is to help a user to fill the form.
Use cases
- Pull an artifact from gitlab or artifactory
- Perform a end user testing
- Pull code from gitlab
A Service Account is a technical account that should be used only to simulate a user or get code/artifacts from a system (ex: ci-cd). Share a service account to develop / create value within in a team is not allowed
What to do ?
First access to PostIT(serviceNow) using this link: Service Account Creation
You should see:
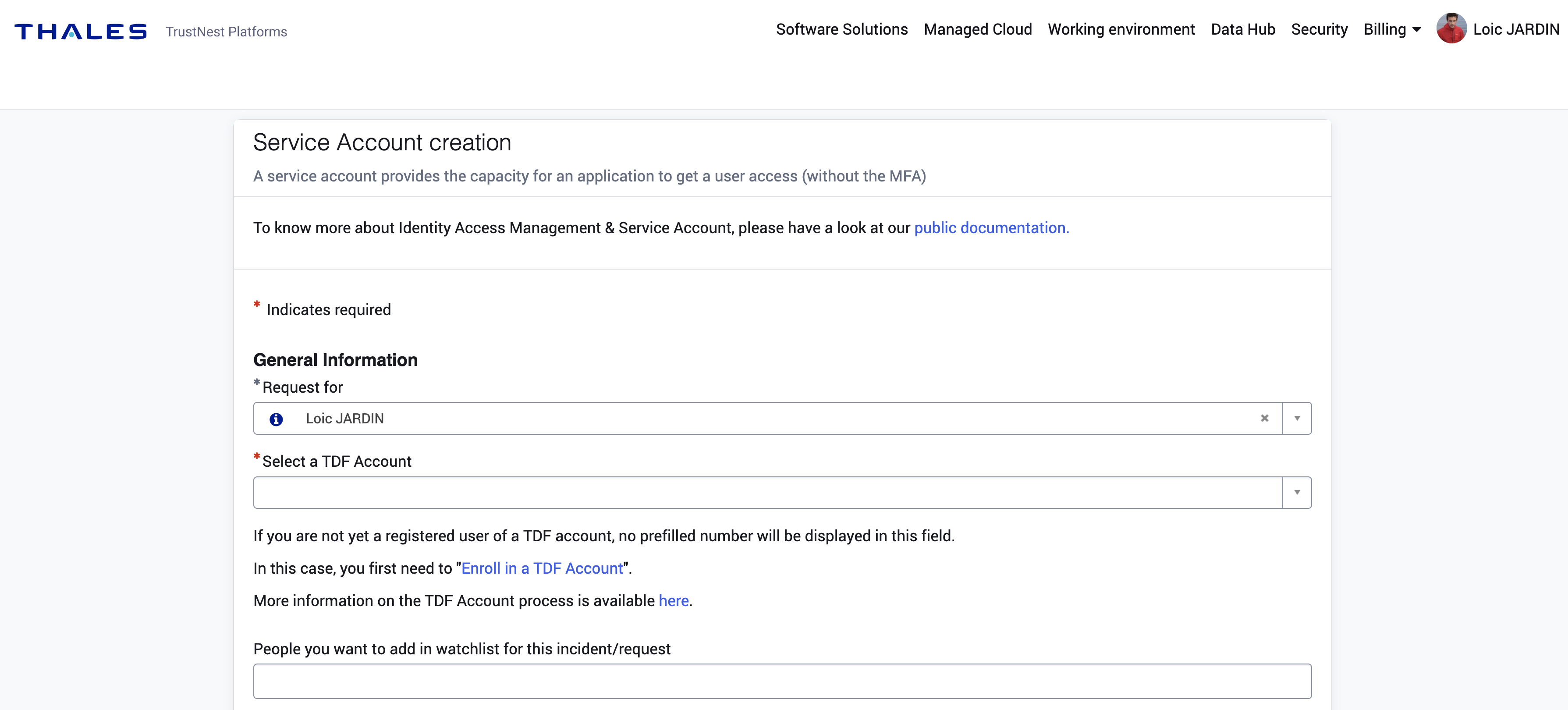
Then, fill the form with the following explanations:
- Project Name: This field will be used to add internal tags on your service account. For instance: Copernicus . Tips: avoid common names like demo, transversal, common etc...
- Service Account Name: Enter the prefix of the service account (before the "@"). For instance: copernicus-cicd for copernicus-cicd@svc.thalesdigital.io
- Project type: This field will be used to add internal tags on your service account.
- Environment type: This field will be used to add internal tags on your service account. For instance: Prod, PoC etc...
- Description: Please, take your time to describe properly the use cases you're integrating.
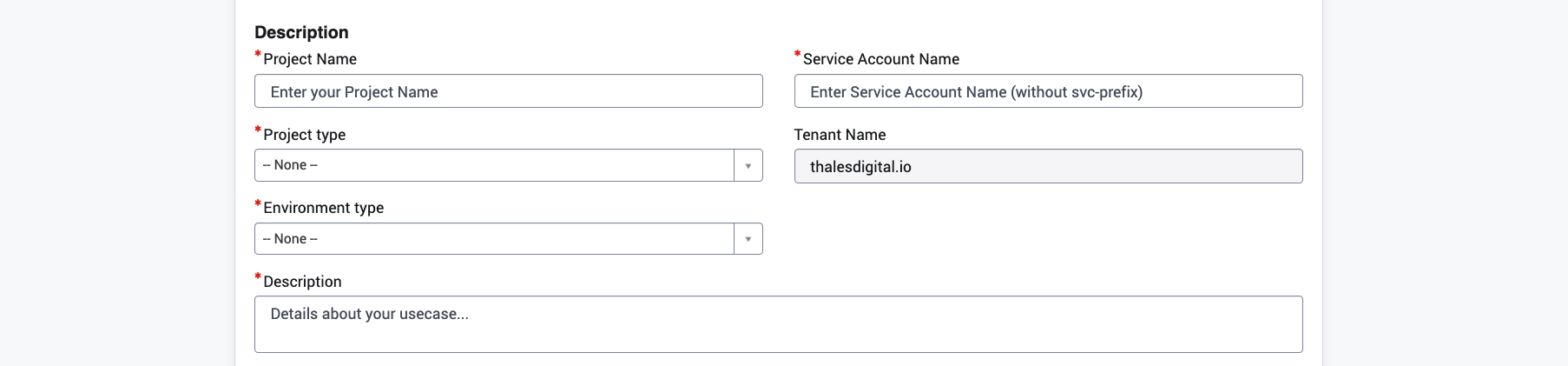
- Hosting Environment: this field describes the service / environment that will use the service account. This is the from.

The Service Account can be used with MFA to access to Trustnest Services (such as Software Factory, or DataLake).
To mitigate the risk of credentials theft, a IP restriction is put in place for all Service Accounts created after Q3 2022.
In order to easily onboard your new service account, we will authorize by default some trusted IPs.
Your new service account will authorized to authenticate when used from:
- Thales Digital Factory (Paris, Montreal and Singapore) main IP addresses.
- Most used Thales Proxy/VPN services, Corporate Network IPs(RIE).
- TDP CoreServices IPs(e.g Zscaler VPN "ZPA", Gitlab runners,...)
If you need to use your new service account from another location or IP, you can request additional IPs whitelistening.
We currently support the follow use cases:
-
Permanent IP(s) whitelisting from Azure IPs: this applies only to the provided PUBLIC IPs that are linked to Azure resources that exist on you subscription(e.g VMs, Load Balancers, WebApps, LogicApps, Azure Functions, AKS).
-
Temporary IP(s) whitelisting: this applies to IP addresses that are found on your azure subscription(e.g home IP when working remotely). These IPs will be authorized only for 48 hours then automatically revoked.
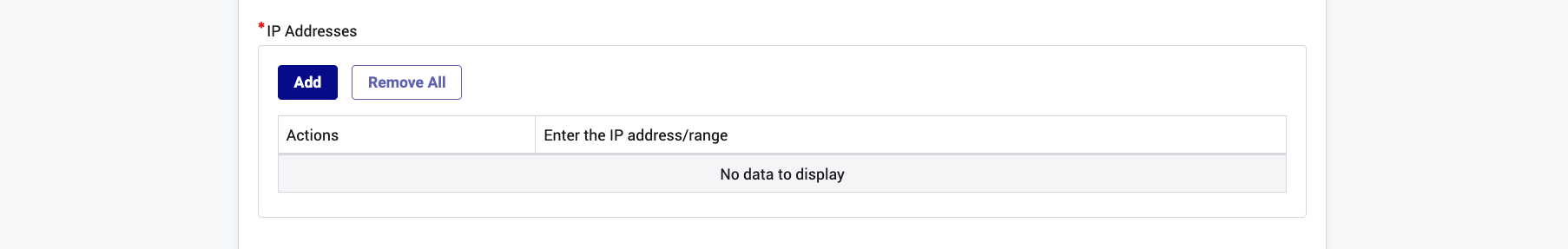
Please provide the source IP addresses that will be used by your service account. (usually Continuous Integration & Continuous Deployment pipeline; or your development laptop for debugging).
- IP Addresses: Provides the IP from where the service account will be used.
HOWTO
Know if my ip is whitelisted ?
First get your public ip using the following command line:
curl ifconfig.me
Then, have a look to the architecture of the current conditional access policies here: Service account Security Policy - auth required
2 choices:
- you're using a Trusted IP: your IP should be already allowed. In case of doubt, send a request using postIT to support team with your IP and the name of your service account. The team will confirm if the IP is considered as Trusted or not.
- you're using an untrusted IP: your IP is blocked. You should send a request using postIT to allow your IP for 48h. Please contact the support with the IP and the service account name
Ask for a new trusted IP
First, have a look to the architecture of the current conditional access policies here: Service account Security Policy - auth required
If your IP is part of Trustnest or a third party: you can send a request to postIT to ask for an update of the policy. If not: even if you send a request, the demand will be rejected.